Some developers always use their development skills to create tools that sabotage the overall functioning of a system, or network, or sometimes infect other computers. One such technique is to use a botnet to bombard requests on a system within a network which eventually leads to choking of the system resources and dishonoring legitimate requests. This sort of botnet attack is called a DoS attack.
While DoS attacks are carried out on a network, there’s also another way to choke resources on a computer that is not necessarily connected to a network through something called a fork bomb.
While the name might sound funny, this is not a new type of threat, and the first fork bomb, also known as the rabbit virus, dates back to 1978 and ran on an IBM System/360. That said, today I will talk about this fork bomb, and whether you should worry about such a threat on your system.
A basic explanation of fork bomb
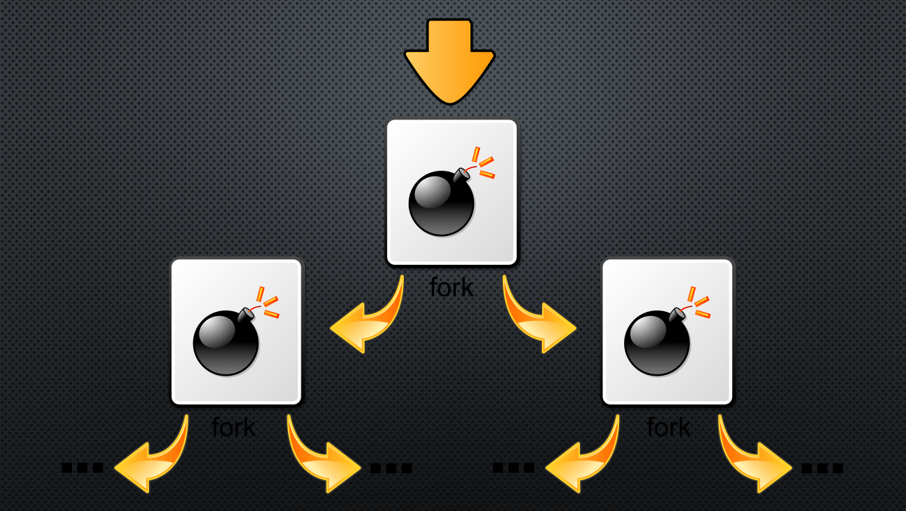
Before talking about fork bombs, you must know about the Fork. No, I am not talking about some cutlery to eat Chinese food, but Fork is basically a type of system call on Unix or Linux systems that replicates an existing process, or the parent process to create a new child process. These two processes can hence run independently and thus, enable faster processing, whenever necessary.
Forking on a Linux system is helpful, but Fork Bomb on the other hand takes it a step ahead where the child processes keep replicating themselves indefinitely, unless all the system resources are used for nothing essential but to execute the command that recursively calls the child process.
Once the attack starts, resources are blocked from allowing any user-initiated or essential system processes, and the inputs from devices such as keyboards and mice aren’t registered, nor you can log out of the system. As the loop continues, system resources are typically exhausted even before the number of processes reaches the maximum number of processes permitted by the system. This eventually leads to a system crash.
When a system crashes due to long inactivity after a fork bomb attack, a hard reboot can solve the issue, while there are chances you will lose your data, if you didn’t save what you were doing. Unless it is not put in autostart folder of the system because after that as you hard restart your PC, the system will automatically activate the Fork Bomb and the loop will go on. Nevertheless, if you know the cause can delete the file by putting the system in Safe mode.
How does a Fork bomb differ from a DoS attack?
In the case of a DoS attack, a botnet is used to attack one or multiple computers over a network. So, the attacks are external in the case of a DoS attack. These attacks typically infect computers on a network, and when the botnet is ready to attack, or at some point in time, it starts bombarding requests on a remote computer.
In the case of a Fork bomb, the commands to run the child processes are run internally within the system and it is not necessary for the system to be connected to a network. Sometimes this can also be run by a user if there are certain errors in the building block of some code that is being written.
Are Windows computers vulnerable to fork bombs?
Windows cannot fork an existing process, and hence only Unix and Linux-based systems, because they can fork processes, are vulnerable to fork bombs.
But that doesn’t mean, similar attacks are impossible on Windows systems. Through meticulous programming, it is possible on Windows to create new processes back to back that will eventually choke the system resources and result in the system crashing.
Unlike fork bombs, it is very complex to write such a code for Windows, if compared to how easily a fork bomb code can be written in most modern programming languages like Python, C, Java, Ruby, etc.
How to prevent fork bomb attacks?
Well, it is obviously possible to prevent fork bomb attacks on a Linux or Unix system, provided there is a limit on the number of processes a user can run. There are many ways to do so. For example, the ‘ulimit=X’ command can be used to set a limit of just X number of programs for the specified user.
The /etc/security/limits.conf file can also be edited to achieve the same, with the additional advantage to set the limit across all the users on the system.
However, it should also be noted that a program having superuser privileges or any other user on the system having administrative privileges can run a fork bomb overriding all the limits set.
So, there’s no one size that fits all way to defeat a fork bomb attack. The users should take basic security measures, and that’s the only way to mitigate the risks. In the case there are some untrusted programs, care should be taken that they aren’t granted superuser privileges when the process limits are in place.
So, that’s all about fork bombs in general. Do you have any questions? Feel free to comment on the same below.
Related Posts
What is a juice-jacking attack? How can we be safe from such attacks?
Getting the right dashcam for your needs. All that you need to know
WhatsApp iPad App Gets Major Overhaul, Adds New Communities Feature
Moto G85 5G launched in India but is unlikely to beat VIVO or XIAOMI
Rise of deepfake technology. How is it impacting society?
Smartphone Apps Get Smarter- Meta AI’s Integration Across Popular Platforms