This section describes the security log or secure log recorded in the Linux OS (CetnOS 8/7, REDHAT). A file that records SSH connections and login operations to the server. By examining the history retroactively, you can investigate whether or not there is unauthorized login.
What are Linux security logs or secure logs?
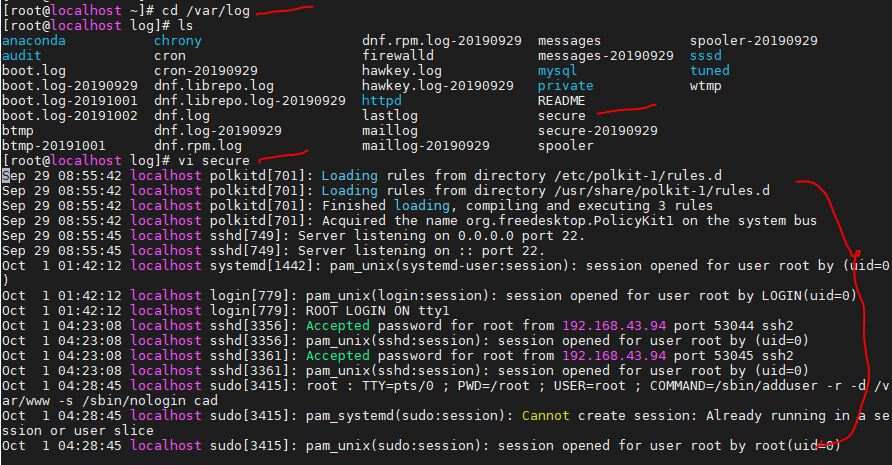
A text file stored in /var/log/secure logging all records security-related information on a computer system is called a secure log file.
If log rotation is set, it may be divided into multiple files. A log related to authentication is also recorded and can be opened only by the root user in the initial state. When the following operations are performed, their time will be written to the file.
Operations recorded in the security log are
- When logging into the server
- When promoted to root with su command
- When using the sudo command
- When the SSH daemon starts/stops
- When you enter the wrong password
- When the SSH connection is disconnected
It is basically a file that the system writes and be careful not to edit it yourself.
Check SSH access in secure log
As mentioned above, investigations related to SSH and login are recorded, so it can also be used to check to see who has got access to your system. Use the below-given command
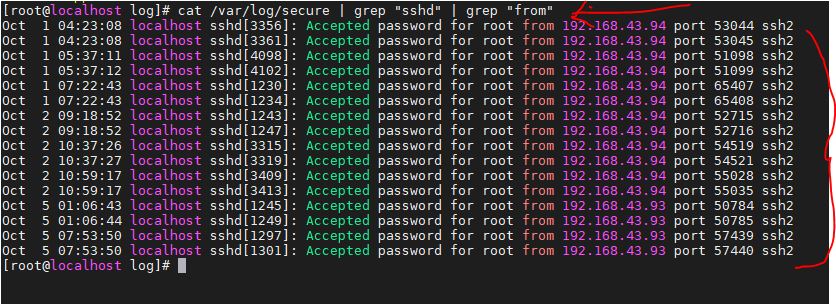
cat /var/log/secure | grep "sshd" | grep "from"
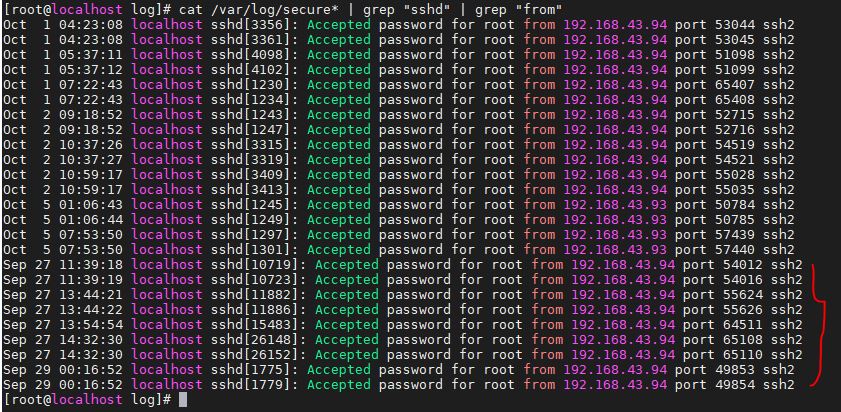
The SSH login history is extracted by performing a grep search on the secure log. In the below screenshot, you can see how many times we had used CentOS 8 Linux system to login via SSH.
Log-rotated past files can also be searched at once.
cat /var/log/secure* | grep "sshd" | grep "from"
If it is compressed with gzip at the time of rotation, zcat can be used with a command to decompress it.
zcat /var/log/secure-* | grep "sshd" | grep "from"
Other articles:
Related Posts
How to create email groups in Gmail? Send one email to multiple recipients in a matter of seconds.
Getting the right dashcam for your needs. All that you need to know
How to Install 7-Zip on Windows 11 or 10 with Single Command
How to Install ASK CLI on Windows 11 or 10
How do you install FlutterFire CLI on Windows 11 or 10?
How to create QR codes on Google Sheets for URLs or any other text elements