Netstat is a nifty tool available on all popular operating systems out of the box including Windows. Netstat is an abbreviation of “Network Statistics“, it is a command line-based utility to check both incoming and outgoing computer connections. Thus, we can use it to see what ports our system is listening on. It can list both TCP and UDP ports, therefore for network administrators “Netstat” is quite a handy tool for network troubleshooting and security audits.
What is Netstat?
Netstat is a command-line network utility available in Windows, Linux, and MacOS. It displays network connections, routing tables, interface statistics, masquerade connections, and multicast memberships.
Netstat Commands to See Listening Ports
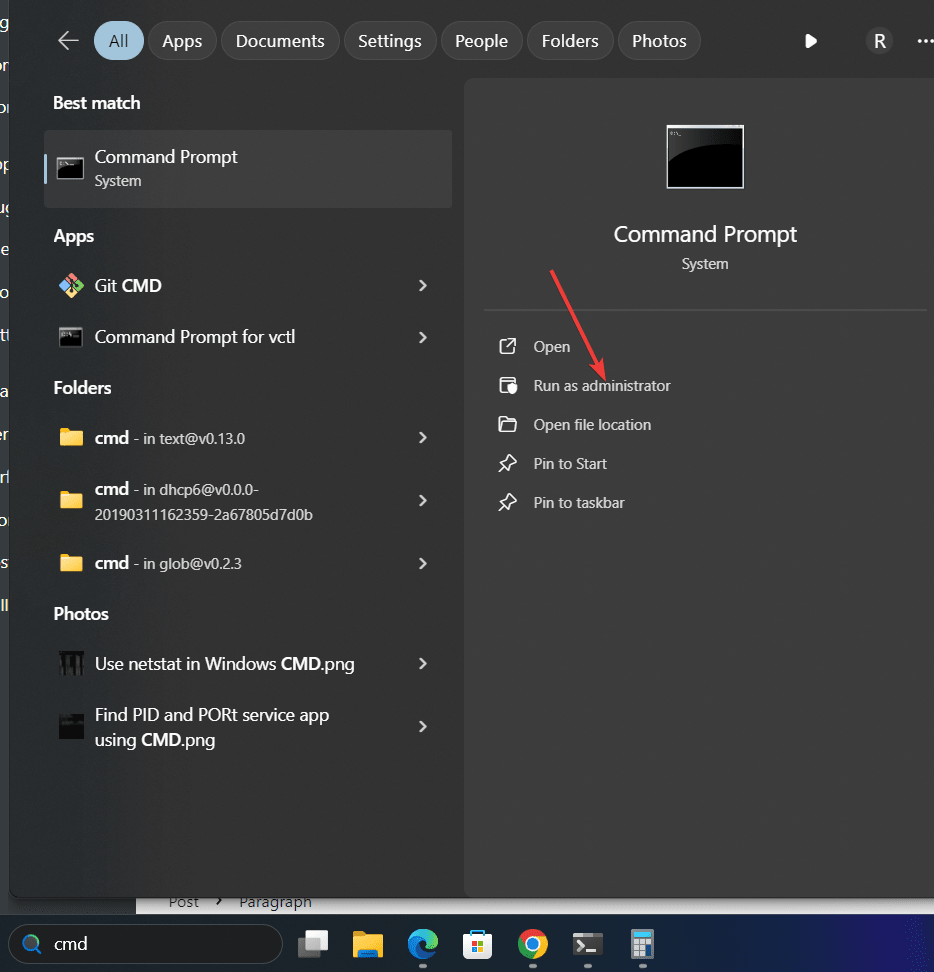
Open Command Line Interface:
If you are using Windows 11 or 10 then open Command Prompt as admin. For that, you can search CMD in the Start menu and when it appears, select the “Run as administrator” option. Whereas, on Linux or MacOS, simply open the Terminal app.
2. Execute the Netstat Command to list all ports
To view all listening ports including others we can use Netstat with the -a option, so to use it, the command will be like this netstat -a. This command will show all active connections and the ports that our computer system is listening on. Although, it will list all the ports but will try to resolve the names for all of them before listing, which could slow down the process of ports listing; to make it a quick add -n option. It will show the actual numerical IP addresses and does not resolve names. So, after adding the -n, the command will be “netstat -an“
netstat -an
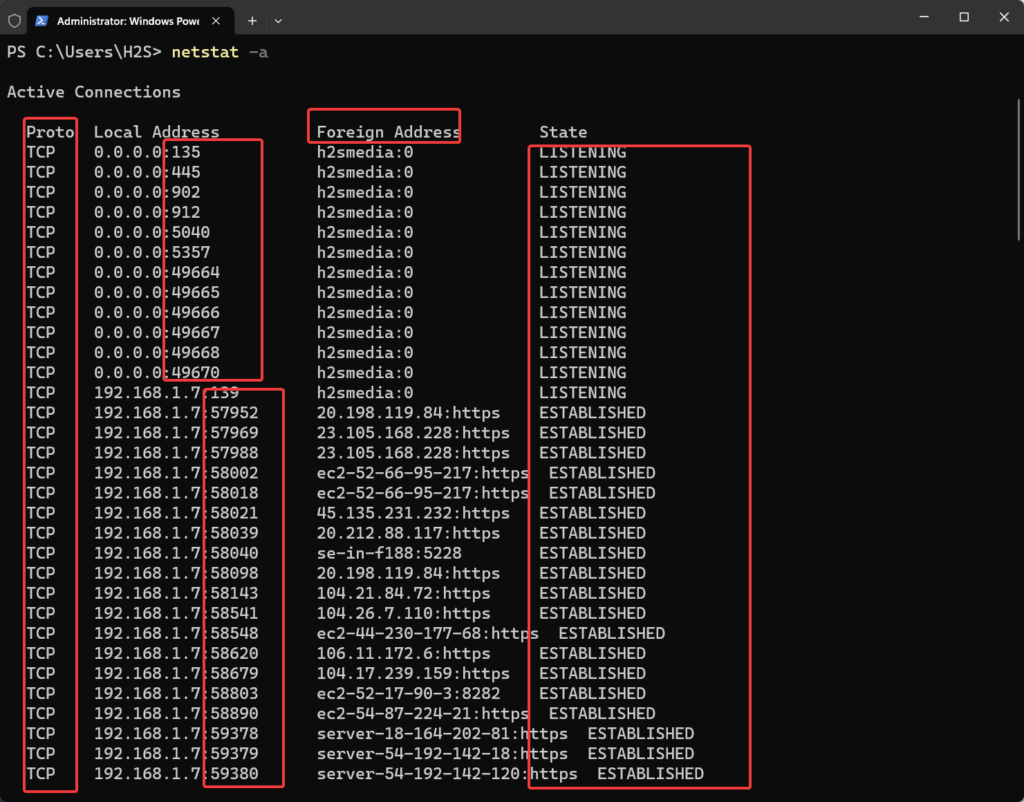
Most of the common information will be there such as showing all ports that are listening for incoming connections including what protocols they are using along with the addresses. The ‘Foreign or Local Address’ column indicates the port number on which the system is listening.
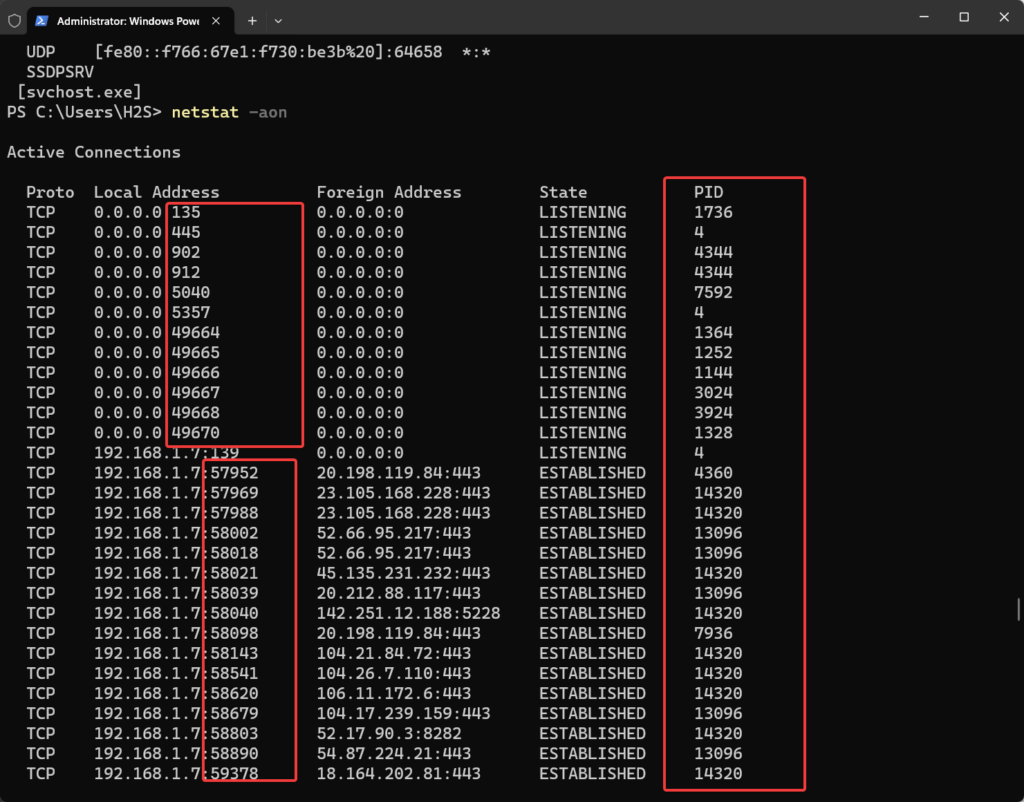
3. Find the Port along with Process IDs
Those who also want to list all listening ports along with the Process ID (PID) can use the command- netstat -aon
Used options:
- -a : Displays all connections and listening ports.
- -o : Displays the owning process ID associated with each connection.
- -n : Displays addresses and port numbers in numerical form
4. Filtering for TCP or UDP Ports:
- Use netstat to only show TCP listening porrts:
If you don’t want a list of all ports instead of protocol-specific then we can use the -p option to make the Netstat filter only the protocol we want. If we use -p along with -s then it can be used for all types of available protocols.
netstat -apn TCP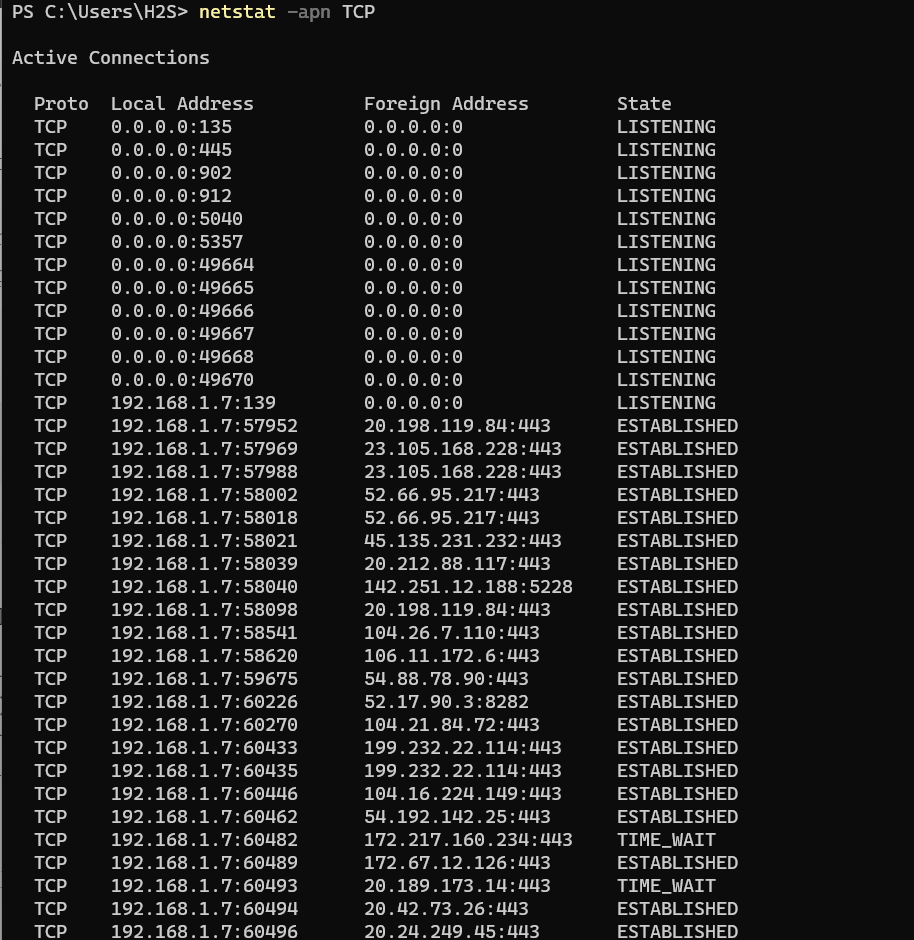
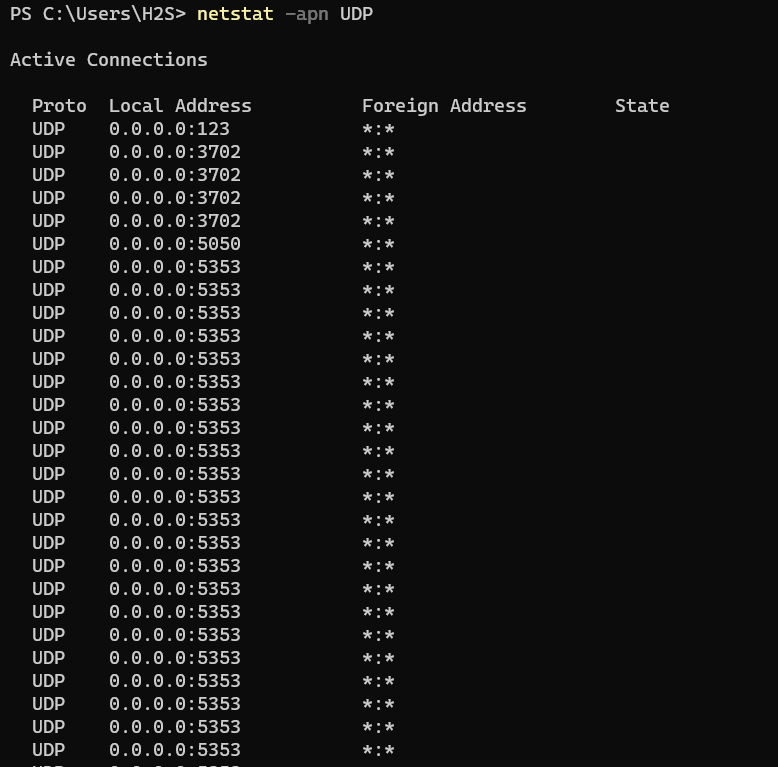
- List only UDP ports using netstat:
Similarly, we can use the above command for UDP and other types of protocols, here is the syntax that can be used:
netstat -apn UDP
Conclusion
Although the functionality of Netstat will be the same across the different operating systems, however, some flags and their results may vary. We have just listed a few options that can be used with Netstat you can explore others by using the command – netsat –help or on the Microsoft learning website.

Related Posts
How to create email groups in Gmail? Send one email to multiple recipients in a matter of seconds.
What is a juice-jacking attack? How can we be safe from such attacks?
Getting the right dashcam for your needs. All that you need to know
How to Install 7-Zip on Windows 11 or 10 with Single Command
Install Google Earth on Windows 11 or 10 Using a Single Command
How to install Gaming Services on Windows 11