DNS over HTTPS (DoH) is a free protocol standard for transmitting DNS requests (and resolutions) over the Hypertext Transfer Protocol Secure (HTTPS). It is a secure alternative to transmit DNS instead of plain text because DOH encrypts the data. This technology is intended to protect the content from unauthorized access or manipulation and to protect the privacy of Internet users. Here in this article we also learn how to enable DNS over HTTPS in Firefox, Google Chrome, Microsoft Edge, and Opera.
Learn how DNS over HTTPS works and the advantages and disadvantages of the standard.
How does DNS over HTTPS work?
The Domain Name System (DNS) links readable URLs with cryptic IP addresses and is one of the most important services of IP-based networks – because meaningful names are easier to remember than bare columns of numbers.
The application-level Domain Name System usually resolves host names based on natural language and provides an associated IP address. For example: When you call up a URL (e.g. www.google.com) in the browser, a request is automatically made to DNS to determine the IP address of the web server (in our example this would be 142.250.192.174). Based on this information, the browser then calls up the website. Without DNS, you would have to enter the address in the browser every time you want to visit a website.
In addition, the DNS allows the IP addresses of servers to be changed comparatively risk-free: If users only handle one DNS name, changes to the associated IP address remain largely unnoticed. One possible application for this is the replacement of classic IP addresses byIPv6. In addition, individual DNS names can also be assigned to several IP addresses – the result would then be a simple load balancing via DNS (load balancing).
The database: Domain Resource Records
The DNS database is organized in the form of resource records. Each individual host and top-level domain can be linked to several of these records. A resource record consists of five entries:
- Domain_name: Name of the domain to which the entry refers.
- Time_to_live: Validity period of the entry in seconds. The value indicates how long the record can be cached in caches (“cached records”) before the data must be updated again from an – always current – “authoritative record”.
- Class: For information about the Internet, the class is always set to “IN”. Other fields are possible but are rarely used.
- Type: Specifies the type of record, such as “A” for an IPv4 address, “AAAA” for an IPv6 address, or “NS” for name servers.
- Value: The value of the entry depends on the “Type” of the record and can take on various values, including a number, a domain name, or an ASCII string.
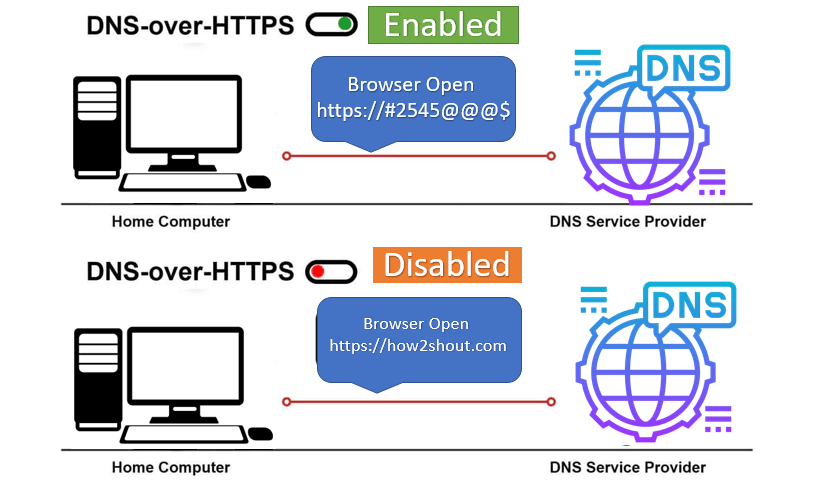
However, there is also a catch: The query to the DNS server is transmitted in plain text. This means that, in principle, on the path between your device and the name server, you can see which website you want to access. This can easily be detected by hackers and cybercriminals to achieve manipulations (e.g. redirecting to another page or DDoS attacks).
This is where DNS over HTTPS comes in. As the name suggests, this uses the HTTPS protocol, which runs on port 443 by default. Since this is open in most networks, there are no problems due to firewall blockades or the like.
The DNS traffic thus runs via an encrypted connection to the (DoH-capable) DNS servers, the so-called DoH resolvers. For this purpose, DoH uses connection-oriented communication and sends HTTPS packets after it has been established, which in turn contain the actual DNS request. The data is thus hidden in the actual HTTPS traffic. The resolver also responds encrypted.
By using HTTPS, virtually any web server is now able to answer DNS queries (provided, of course, it supports DoH). In addition, it should provide information about all linked and used pages on the requested website in the future. This eliminates the need for further DNS queries when you move around the pages.
DNS over HTTPS also has a disadvantage
The majority of “normal” Internet users probably don’t even know how DNS works and what exactly it is needed for. For all those, DoH is certainly a huge gain in security. Administrators and tech-savvy home users are likely to view the whole thing with mixed feelings.
Especially in companies, the influence of DoH can sometimes even lead to serious difficulties. Typically, system administrators use local DNS servers and DNS-based software to filter and monitor local traffic. This is primarily intended to prevent employees from accessing unauthorized or dangerous content. With DoH, however, employees are able to bypass the filters and can also access blocked content.
And the security of your privacy is not one hundred percent guaranteed at DoH. Although the data is encrypted in both directions on its way between the client and resolver, providers also have other options available (keywords “TLS handshake” and “SNI”) with which they can track the history of your visited websites.
Hence, there is also an alternative to DOH which is DOT (DNS over TLS) protocol, however, the standards of encryption will be the same in the two only the difference will be in terms of methods used for encryption and delivery.
Which browsers already support DoH?
Enable DNS-Over-HTTPS on Mozilla Firefox
Mozilla and the security service provider Cloudflare are the driving forces behind DNS over HTTPS, which is why Firefox (in 2020) was also the first browser with integrated DoH.
How to enable DNS over HTTPS in FireFox?
- Open the Mozilla FireFox browser
- After the open the Settings page and then select General from the left side given menu.
Alternatively, you can paste about:preferences#general in your browser’s URL bar to open General Settings directly.

- After that click on the Network Settings button.
- And scroll down to check the box given to Enable DNS over the HTTPS option in Mozilla FireFox.
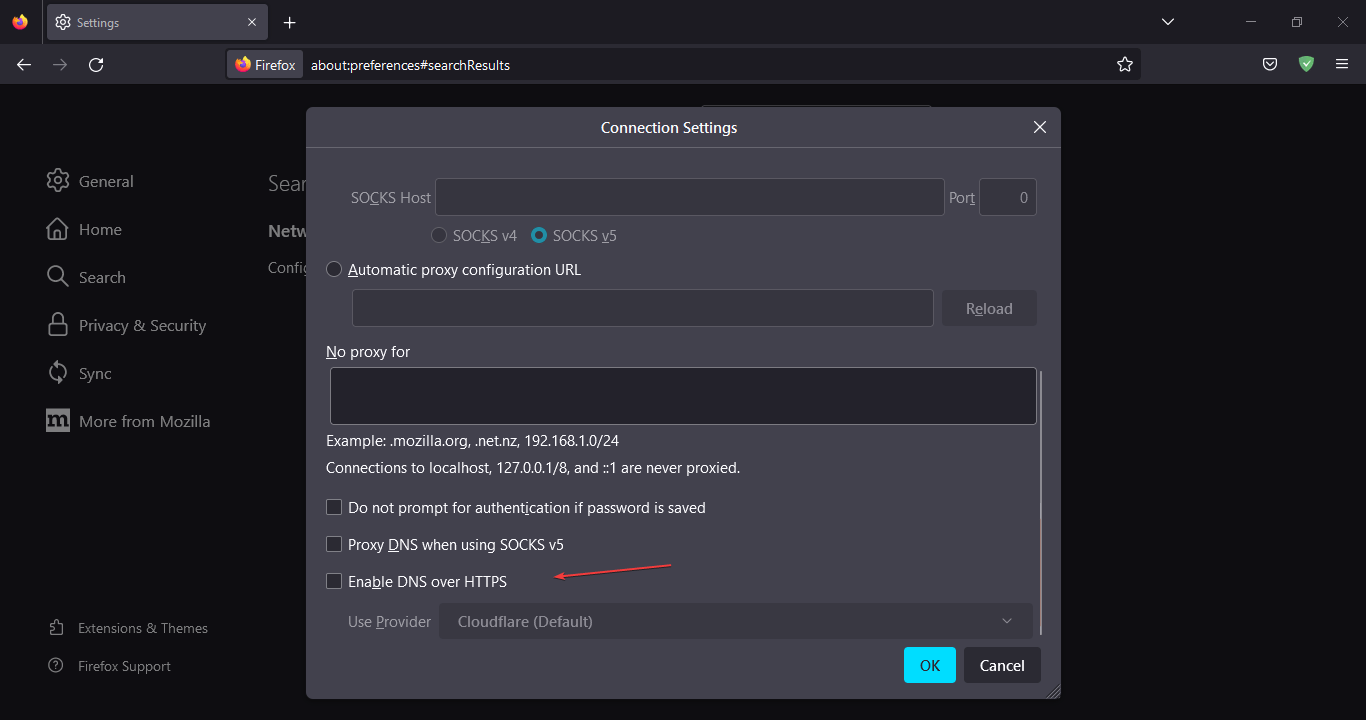
Tip: Firefox handles all DoH requests through a Cloudflare resolver by default. Personal settings regarding DNS handling are simply ignored. Alternatively, it is possible to set the setting to another Publicly available server’s DoH resolver using the Custom provider option.
Enabel DNS-over-HTTPS in Google Chrome
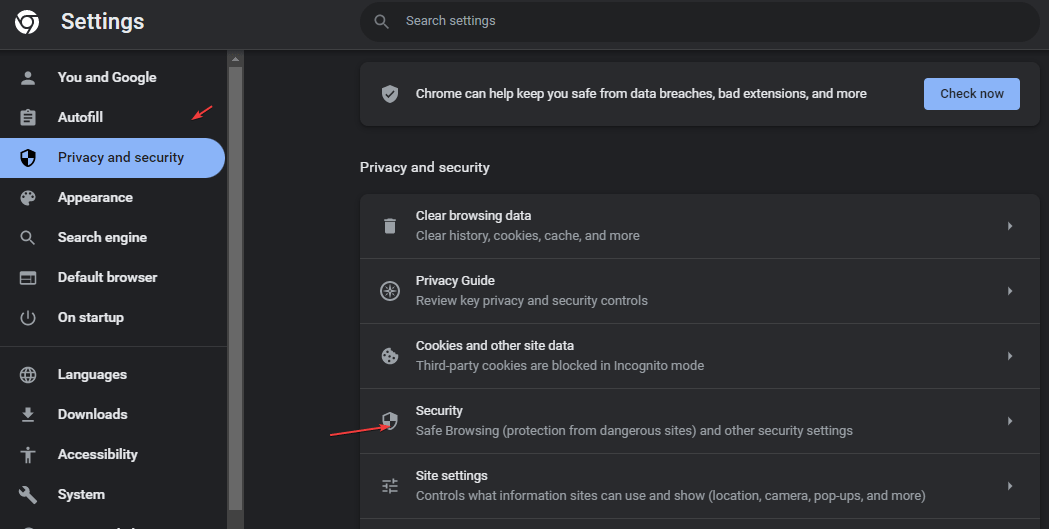
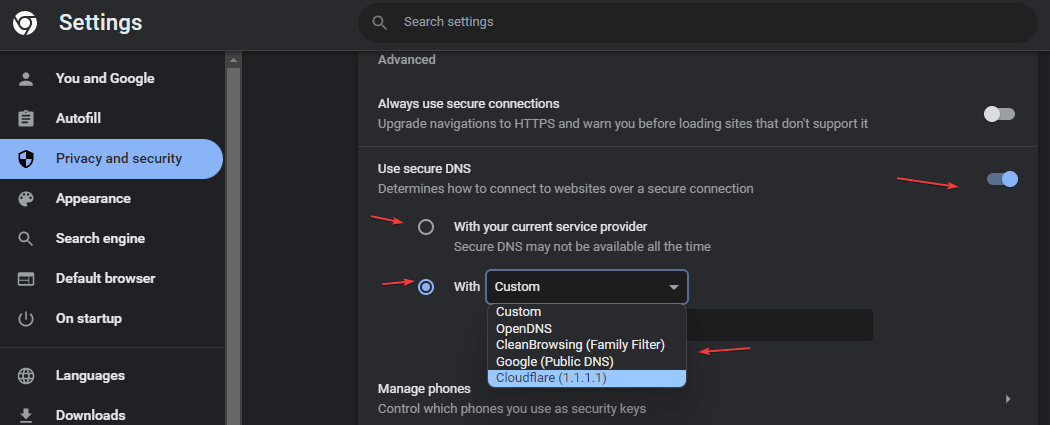
After Firefox, Google Chrome is the second browser to be equipped with DoH. DNS over HTTPS is available in Google Chrome since version 83 for Windows and macOS. We can enable or disable it from the Security Settings of the browser. Currently, this already works for Windows, Mac, Linux, Android, and Chrome OS.
After turning on the feature, Chrome sends the DNS requests to the same server as before but encrypts the traffic if it has a DoH-enabled interface. If this is not the case, the requests are sent unencrypted. If your current DNS service provider doesn’t support DOH, then use the Custom service provider from the list.
To quickly open the Settings use this URL- chrome://settings/security
Enable DNS-over-HTTPS in Microsoft Edge
- Although just like Google Chrome, DNS-over-HTTPS will also be enabled in Microsoft Edge browser, however, if you want to set a custom one then here are the steps to follow.
- In your browser’s URL box copy-paste
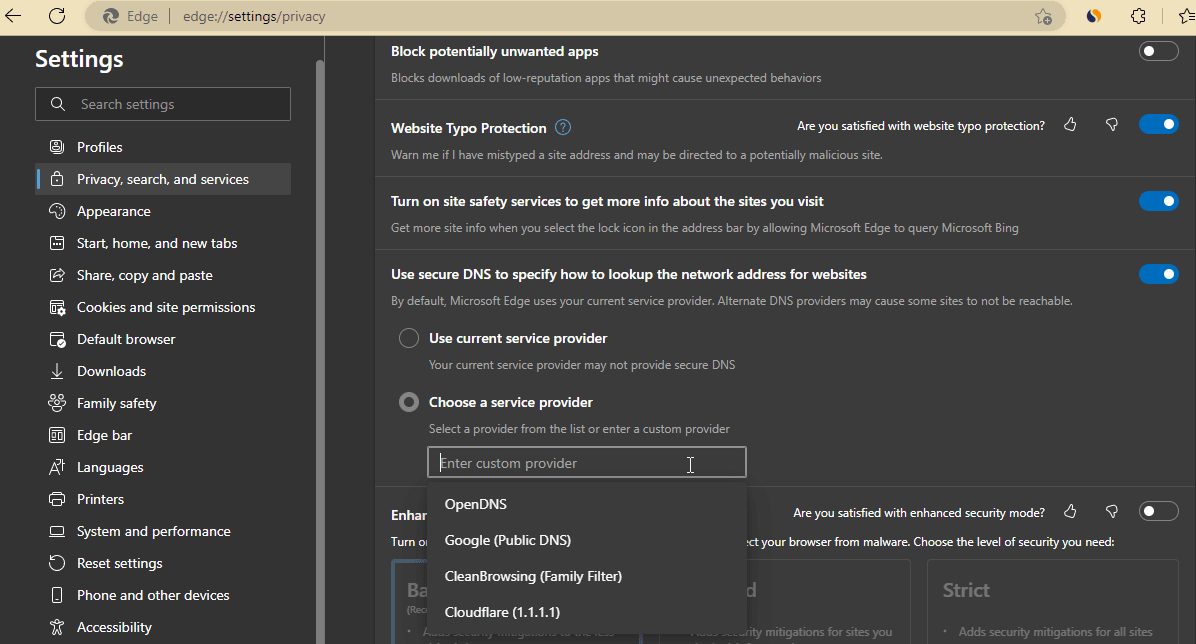
edge://settings/privacyand hit the Enter key. - After that scroll down to the “Use secure DNS to specify how to lookup the network address for websites” settings.
- Select Choose a service provider option and select the listed providers or add one of yours.
Secure DNS For Chromium-based browsers
Many other well-known browsers (including Opera, or Vivaldi) are based on chromium and its Blink engine. DNS over HTTPS is therefore also available with these and can be activated in the respective settings as we have done for Chrome.
Note: Apple’s iOS 14 and macOS 11 released in late 2020 support both DoH and DoT protocols
How to Check DNS OVer HTTPS using Cloudflare
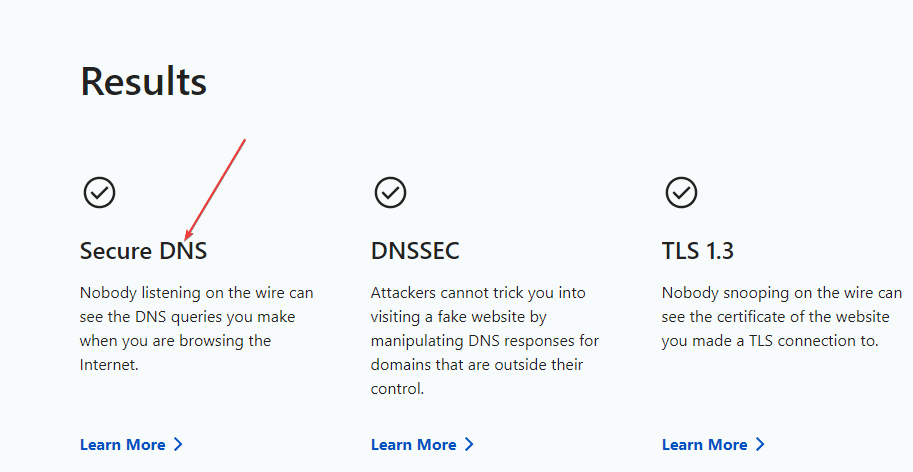
After enabling the Secure DNS or DNS Over HTTPS in your browser, we can check to confirm whether we are actually on a secure DNS service or not. For that Cloudflare provides a service called – Browsing Experience Security Check. Use the link and open the page. There click on the “Check My Browser” button. Soon you will have the result:
FAQ
DoT uses TLS (Transport Layer Security) instead of HTTPS to transmit requests and requires port 853 to be enabled. This makes communication easier to identify and prevent.
Unfortunately, DoH does not offer complete protection of your privacy either. For Internet Service Providers (ISPs), it is still possible to record unencrypted components of communication.
DoH is an IETF standard or RFC draft. The IETF (“Internet Engineering Task Force”) is a non-profit organization responsible for adopting public Internet standards.
Other Articles:
How to add Cloudflare to VPS/ Dedicated / Shared hosting
How to change the DNS server on all Android devices without getting root access
How to use a preferred DNS over TLS on Google’s latest Android
How to set up a Dynamic DNS server to control your home
Related Posts
What is Identity Theft? All that you should know about this form of cybercrime
Guardians of Data: How Role-Based Access Control Reinvents Security
What are the main five types of Cybersecurity?
Does Windows 11 need an antivirus along with Windows Security?
Which is better Cloud hosting or WordPress hosting?
Top 10 Free Open Source Blogging Platforms or CMS in 2023