We know the term Hacking and usually, it is done by hackers to harm someone by accessing their system or smartphone. But Ethical Hacking is more like a permitted task to know the weaknesses within a system or network.
To perform this type of practice, we seek help from tools that can locate the soft points from any system as well as from the servers or web applications by running it. And we know them as Ethical Hacking Tools.
Many organizations use it to know and rectify the loopholes in their networks or computer systems to prevent any sort of security breach. The existence of this similar type of tool is not short in terms of quantity. That is why we created a list consisting of 5 Ethical Hacking and testing Tools to ease your search efforts while finding one. Check out the list.
Probely- Web Vulnerability Scanner
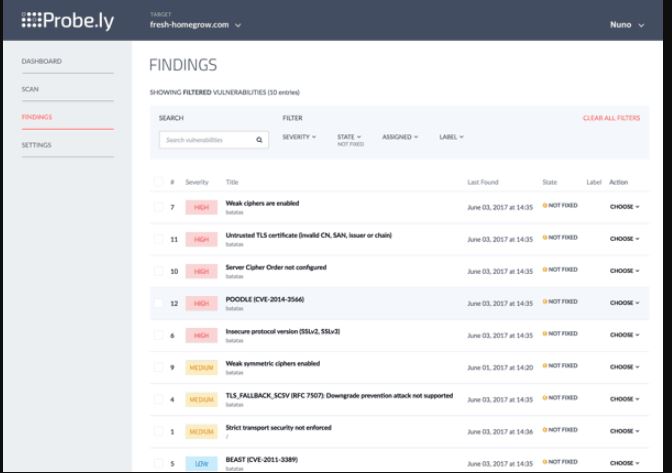
Probely is a Web Application Vulnerability Scanner that secures your system or network by scanning it in a constant mode. You can cope with vulnerable aspects throughout its wheel of life by using this tool. If you seek some mentorship to sort out the issues then this is the tool to get that service. It is architected to fit for the developers to ease the tension of any breaches.
Features
- Using it will allow you to scan SQL Injections and XSS with more than 5000 weak points.
- We can even scan WordPress via this.
- It has all the tools for compatibility with API.
- There are PDF data for security display available.
Price: Paid
Acunetix
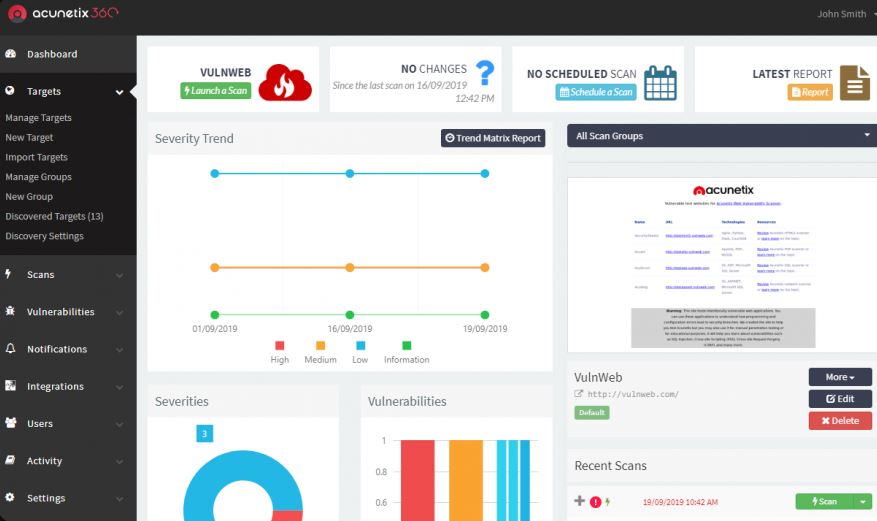
This is one of the most intelligent web application security tests that can copy any hacking activity to get the upper hand for the motto of keeping things safe. HTML and JavaScript will be in full protection if you use their accuracy of scanning for them. The vast range of auditing capabilities can check the issues and reports of networks. Even you can scan the apps with a valid certification.
Features
- This also scans for SQL Injection and XSS just like Probely.
- It can point out WordPress weaknesses of plugins, themes, etc.
- It has the feature of working faster and covers a large scale of pages error-free.
- The presence of a Cloud solution is proof of it.
Price: Paid
John the Ripper
If you are concerned with the security of any password then John the Ripper is the one to help you in this matter. It is quite popular and effective for testing the strength of a password and it works best in this field. It can change the algorithm of any password by the auto-detecting mode with the nature of encryption used for the passwords. Thus John the Ripper, a free and Open Source password cracker software shows its intelligence as a tool that can crack passwords smartly.
Features
- The encryption hacking system is one of the best parts of it.
- The open-source availability is a plus point.
- It can work on multiple platforms including Mac or Linux.
- Technical intelligence is there to help.
Website: John the Ripper
Price: Free
Nmap
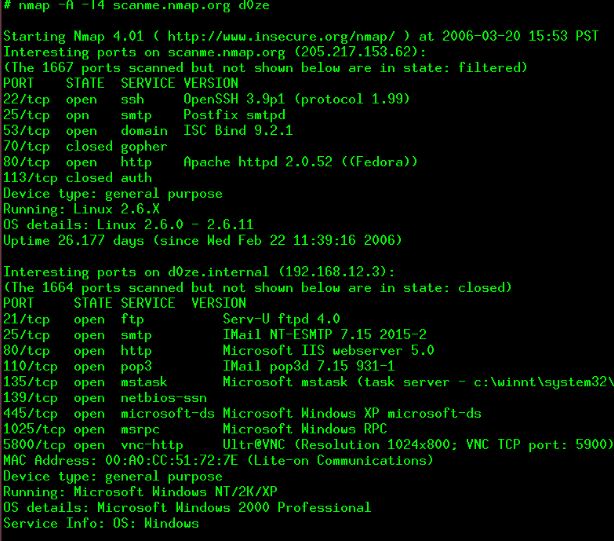
This open-source Ethical hacking tool works on the security of Hosts (local or remote) to maintain the OS along with network management. You will be able to audit the whole process by this. The updates of the tool are very much available on a particular timetable and improving its functionality over the years, even tool is one the matured ones in the market. You would not be disappointed by this because it can deliver things for the sake of any security of system or network with effective results.
Website: Nmap
Price: Free
Features
- It is a type of audit device security.
- Nmap can mark the soft ports in any remote host.
- It is very reliable for the mapping of the network.
- The power of detecting any vulnerability is quite impressive. It works on any network to find such flaws.
- The nature of the tool can support Linux, Mac as well as Microsoft Windows.
Metasploit
Metasploit is an open-source security vulnerability detection tool that helps security and IT professionals identify security issues, verify vulnerability mitigations, and manage expert-driven security assessments to provide true security risk intelligence. These features include smart development, code auditing, web application scanning, and social engineering. The team worked on their findings in Metasploit and the comprehensive report.

Features:
- The extensible model integrates load control, encoders, non-operational generators, and vulnerabilities.
- Provides a strong guarantee for automatic vulnerability detection.
- Metasploit comes with hundreds of vulnerabilities.
- The Metasploit framework can import data from a vulnerability scanner
- It uses an open-source security tool, Armitage.
- And more…
Website: Metasploit
Price: Free and Pro
Aircrack-ng
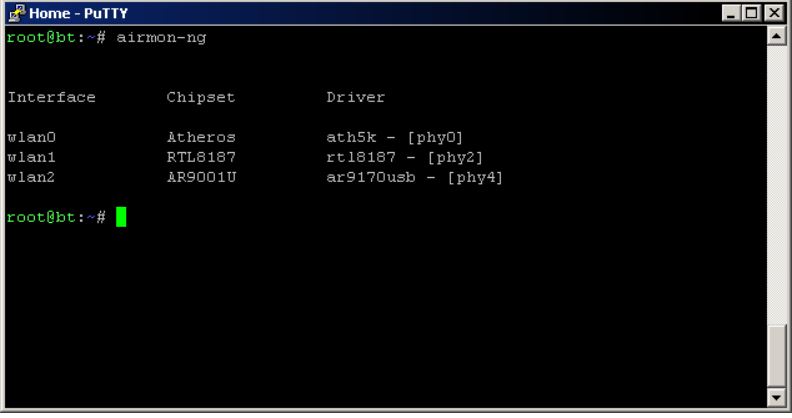
Aircrack-ng is a security software related to 802.11 standard wireless network analysis. The main functions are network detection, packet sniffing, WEP, and WPA / WPA2-PSK cracking. Aircrack-ng can work on any wireless network card that supports listening mode and sniffs 802.11a, 802.11b, and 802.11g data. The program runs on Linux and Windows. The Linux version has been ported to the Zaurus and Maemo system platforms, and the proof of concept is portable to the iPhone.
Features:
- Packet sniffing: transfer wireless network data to PCAP or IVS file and display network information
- Set the network card to monitor mode
- Crack WEP and WPA ( dictionary attack ) keys
- Save and manage the ESSID password list and calculate the corresponding keys
- Allow different processes to access the wireless card.
- And more…
Website: AirCrack-ng
Price: Free
ettercap
ettercap is a tool that can help you capture network packets. On the network, there are often some virus attacks. Some of these attacks are based on the analysis of LAN data packets. When a user sends shared data, others will be able to find it and can add their own APR request after modification, to obtain the host IP of the other party and obtain the MAC address of the computer; the tool used is the APR production tool. Helps you sniff the LAN data, monitor router addresses, and send virus attacks, so you can monitor the network data you need to check at any time.
Features:
- Can scan the host address of the LAN
- Support sending all IP requests with one click
- Using a unified sniffing method
- Can attack the computer’s core IP
- Can insert various MITM attacks once
- It can use external attacks to network data
- Support virus tools to prevent virus intrusion
- Support virus scanning, automatically detect virus packets
- Support sending virus files to different hosts
- And more…
Website: Ettercap
Price: Free
Wireshark
Wireshark is a real-time network analyzer that you can have via the free open-source medium. It can detect and solve any network security-related issues with a success rate for its ability to search the problems and solve them with responsibility. And that is why we can see the popularity of it among the users. The users can understand the problems it fetches from the network because it shows it in a format that users can read without any difficulty. It is very helpful to fetch any vulnerability in the network.
Features
- You can see the inspections while in offline mode because it records the analysis.
- It can be considered as a pocket browser.
- The tool has a powerful GUI.
- It can inspect the GZIP files.
- Wireshark can read multiple formats of files such as Microsoft network monitor, Sniffer Pro, etc.
- Nearly 2000 types of network protocols, Wireshark supports.
- You can use it in main operating systems like Mac OS X, Linux, and Windows etc.
Website: WireShark
Price: Free
Verdict
This type of tool helps many companies to develop and maintain a good security system for them and for the customers with any loopholes in the system that might be easily breakable by any hacker. The popularity of the tools is very high for the benefits we get from them. The drill of testing the network security is easier just because of the services an Ethical Hacking Tool provides to maintain it properly. And we can rely on them without any doubt in mind. The benefits are high if we use them to protect our systems and networks. We must remove the vulnerability in the network for its betterment.
Wrapping up
The 5 Ethical Hacking or testing Tools I mentioned in the conversation are very good for the purpose and you can professionally manage your networks or systems to avoid any obstacle that could hamper the flow of maintenance or services.
Related Posts
What is a juice-jacking attack? How can we be safe from such attacks?
What is ipconfig on Windows CMD used for?
How to install Winget package manager in Windows 2022 Server
How to View Listening Ports Using Netstat
How to Install Pygame Zero on Windows 11
Single Command to install Android studio on Windows 11 or 10