On the Linux operating system such as CentOS 7 and CentOS Linux, the FirewallD is a default firewall management tool. It acts as the front end of the Linux kernel’s Netfilter framework through the iptables command, providing firewall functionality as an alternative to the tables service. The name FirewallD follows the Unix convention of the naming system daemon by appending the letter “d”, which is written in Python.
Since CentOS 7/8, the startup script for the iptables service has been ignored. And need to be used firewalld instead of iptables service. In a similar way, in RHEL 7/8, the default is to use firewalld to manage the netfilter subsystem, but the underlying command is still iptables.
Firewalld is a front-end controller for iptables that implements persistent network traffic rules. It provides a command-line and a graphical interface.
Comparison of Firewalld and iptables:
1. Firewalld can dynamically modify a single rule or manage the ruleset, allowing updates to the rules without breaking existing sessions and connections. Whereas in iptables, after modifying the rules, it must be fully refreshed to take effect.
2. Firewalld uses regions and services instead of chained rules.
3. Firewalld default is rejected, you need to set it later to release. And iptables is allowed by default, and you need to reject it to limit it.
4. Firewalld itself does not have the function of a firewall, but like iptables need to be implemented through the kernel’s Netfilter. That is to say, Firewalld is the same as iptables, their role is to maintain the rules, and the real use of the rules is the kernel’s Netfilter. Only the results of firewalld and iptables and the method of use are different!
Firewalld is a wrapper for iptables that makes it easier to manage iptables rules. It is not a replacement for iptables, although the iptables command can still be used for firewalld, it is recommended to use only the firewalld command for firewalld.
How to Install FirewallD on Linux
If your CentOS doesn’t have firewalld then you can install it using the below commands and then enable + start the same.
sudo yum install firewalld sudo systemctl enable firewalld sudo firewall-cmd --state
Few FirewallD basic commands:
All command need a root or sudo rights user.
systemctl start firewalld # to start the FirewallD service on the system
systemctl restart firewalld # For restarting the service
systemctl enable firewalld #to enable it at boot level, thus it automatically start when a system booted up.
systemctl stop firewalld # Stop the service
systemctl disable firewalld #disable the firewall
firewall-cmd --state #View the running status
firewall-cmd --zone=public --list-ports #View open port
Commands to open the daily port of the website on CentOS Linux
Here are commands that one can use to open some common ports on CentOS Linux server
firewall-cmd --zone=public --add-port=22/tcp --permanent
firewall-cmd --zone=public --add-port=80/tcp --permanent
firewall-cmd --zone=public --add-port=443/tcp --permanent
firewall-cmd --zone=public --add-port=3306/tcp --permanent
In the same way, we can open any port, just what you have to do replace the port number in the above command with the one you want to open.
Open UDP port
Just like TCP ports, we can open UDP port for public access using the below command:
firewall-cmd –zone=public –add-port=443/udp –permanent
Command meaning:
--add-port=80/tcp #Add port, this is used to specify which port/communication protocol has to open --permanent #Permanently effective, no failure after restarting this parameter --zone #Used to specific networking environments public, private or local
Let’s talk a little bit more above the network environment:
By dividing the network into different areas, an access control strategy between different areas is developed to control the flow of data between different program areas.
For example, the Internet is an untrustworthy area, while the internal network is a highly trusted area.
The network security model can choose to initialize during installation, initial startup, and network connection for the first time. The model describes the trust level of the entire network environment to which the host is connected and defines how new connections are handled.
Initialization area:
block: Any incoming network packets will be blocked;
work: Believe that other computers on the network will not harm your computer;
home: Tell that other computer on the network will not harm your computer;
Public area (public): Do not trust any computer on the network, only choose to accept incoming network connections.
Isolated Area (DMZ): Also known as the demilitarized area, a layer of the network between the internal and external networks acts as a buffer. For isolated areas, only choose to accept incoming network connections.
Trusted zone (trusted): All network connections are acceptable.
drop: Any incoming network connection is rejected.
internal: Trust other computers on the network without harming your computer. Only choose to accept incoming network connections.
external: Do not trust other computers on the network and would harm your computer. Only choose to accept incoming network connections.
The default area of firewalld is public.
Firewalld configuration method
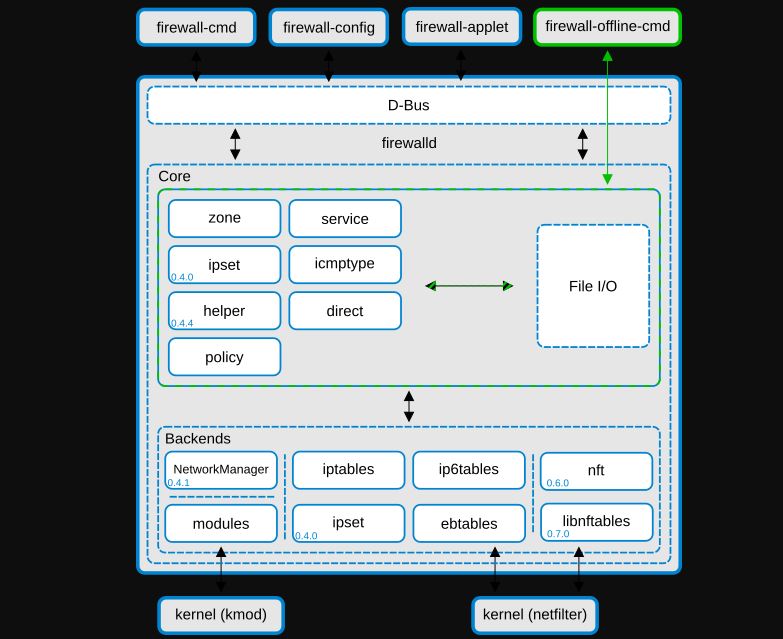
There are three main firewalld configuration methods: firewall-config (graphics tool), firewall-cmd (command-line tool), and direct editing of XML files.
To install a Graphical tool to manage firewall here is the command:
yum install firewalld firewall-config
Firewalld is configured using XML. Unless you have a very special configuration, you don’t have to deal with them, you should use firewalld-cmd.
Configuration file:
/usr/lib/firewalld #Save the default configuration to avoid modifying them.
/etc/firewalld #Save the system configuration file, you will override the default configuration.
/usr/lib/firewalld/zone/ -Firewalld provides nine zone configuration files by default: block.xml, dmz.xml, drop.xml, external.xml, home.xml, internal.xml, public.xml, trusted.xml, work.xml
Few other commands to play around this Linux Firewall.
firewall-cmd –help #Show all available firewall commands
firewall-cmd –version
firewall-cmd –state
firewall-cmd –get-active-zones # View the area used by the network interface.
firewall-cmd –zone=public –list-all #Show all configurations in the specified area.
firewall-cmd –list-all-zones #List all zone configurations
firewall-cmd –get-default-zone #View default area
firewall-cmd –set-default-zone=internal #Set the default zone
firewall-cmd –get-zone-of-interface=eth0 #View the area to which the specified interface belongs.
firewall-cmd –zone=public –add-interface=eth0 #Add interfaces to the zone, the default interfaces are all public, permanently valid plus –permanent , then reload
#Need to be permanently valid, add –permanent
firewall-cmd –panic-on|off #reject |open all packages
firewall-cmd –query-panic #View whether to reject
firewall-cmd –reload #Update firewall rules without disconnecting
firewall-cmd –complete-reload #similar to restarting update rules
firewall-cmd –zone=dmz –list-ports #View all open ports
firewall-cmd –zone=dmz –add-port=8080/tcp #Add a port to the zone
Firewall-cmd –get-services #View the default available services
Firewall-cmd –zone=zone –(add|remove)-service=http –permanent #Permanently enable or disable HTTP service
Firewall-cmd –zone=public –add-port=123456/tcp –permanent #Add TCP traffic for port 123456
Firewall-cmd –zone=public –add-forward-port=port=80:proto=tcp:toport=123456 #Forgoing traffic from port 80 to port 123456
Use with the service
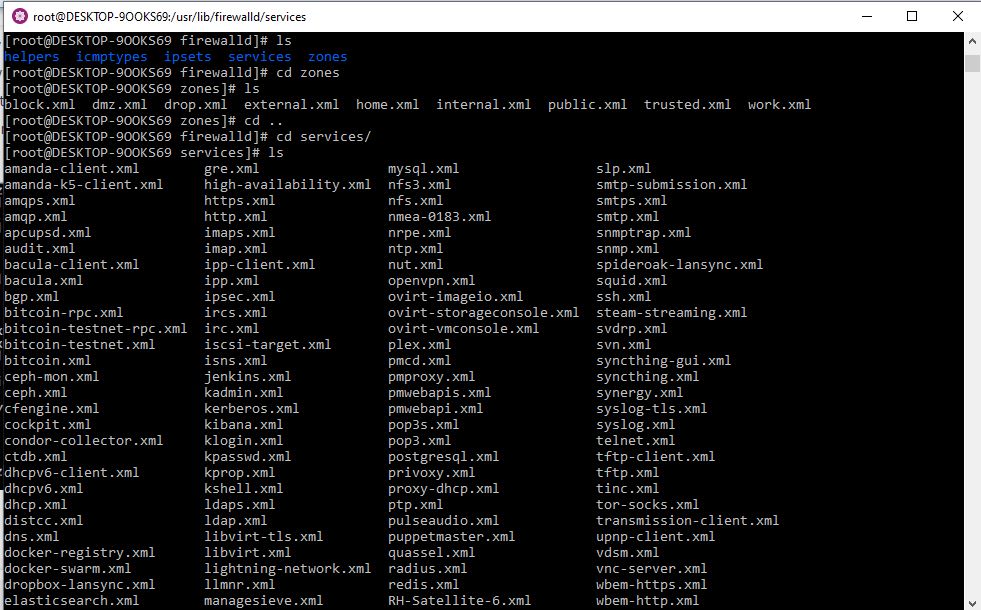
Firewalld has default services that can be used to allow traffic from any specific web application or network service. All the default service files are located at /usr/lib/firewalld/services and the user-created service files for firewall are available under /etc/firewalld/services .
By Guest author: Amreno Namish
Other Articles:
Related Posts
What is Identity Theft? All that you should know about this form of cybercrime
Download Visual studio code portable for Windows 11/10 or Linux
How to install BetterCap on Windows 11 or 10
Google to display only interest-based ads using a privacy sandbox
Ethical Considerations in Digital Banking: Privacy, Data Ethics, and Responsible AI
How to Check if an Android App is Safe to Download?