Latest Work

How to create email groups in Gmail? Send one email to multiple recipients in a matter of seconds.
We often need to send one email to multiple recipients. It can be a promotional email to all ...

We often need to send one email to multiple recipients. It can be a promotional email to all ...

Cybersecurity is the practice of safeguarding organizations and individuals against cyber threats and unauthorized … Read more

CoSoSys is a developer of endpoint-centric Data Loss Prevention (DLP) solutions and security software. … Read more

Incognito mode is a tool to protect your online privacy. In a browser, it … Read more

Internet is one of the greatest things that surely revolutionized the whole world and … Read more
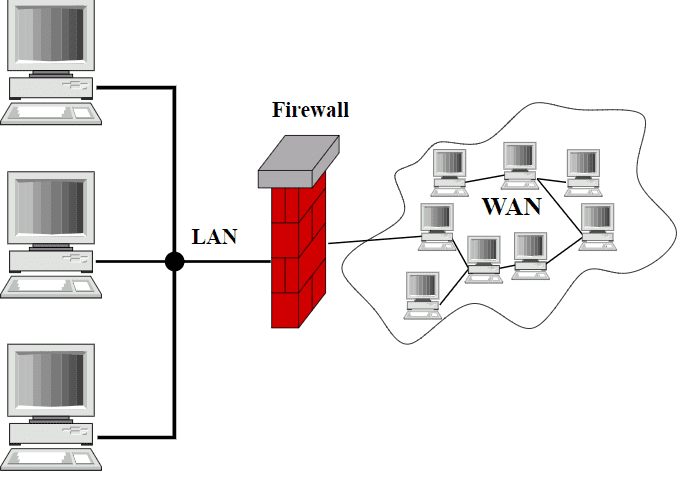
A firewall- as the name indicates- is a Fire like Wall that protects your … Read more

We’re sure you’ve seen a flurry of news reports and lengthy social media posts … Read more
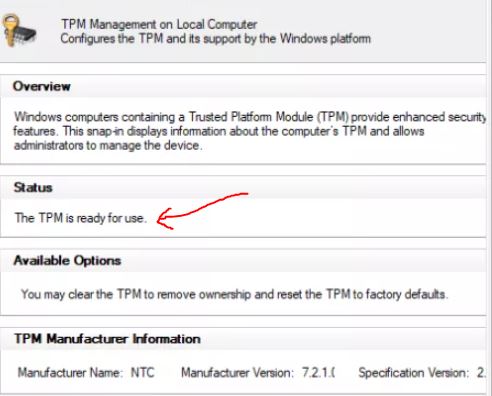
TPM 2.0 stands for Trusted Platform Module, it is an encryption chip that needs … Read more

When your parents asked you to not accept anything from strangers, they were foreshadowing … Read more

Malware is not at all an alien term, rather it is one of the … Read more

The term ‘Phishing’ might not be very common with most people, while some of … Read more

By Zakir Hussain- Director, BD Software Distribution The expression “you are part of something … Read more

In today’s’ world I don’t have to apprise how crucial the security of network … Read more

If you want to maintain your privacy on the Internet, one of the best … Read more