The Parano Protocol uses a combination of four different well known asymmetric algorithms used in a very deliberate technique to leverage existing computational resilience. It is a post-quantum cryptographic protocol that designed to thwart the high degree complex security attacks. Novel use of those algorithms introduces a continuous and variable key generation process creating a multi-dimensional the computational challenge to resist computational brute force attacks. The maturity and stability of the asymmetric encryption’s schemes in themselves are highly efficient and resilient with their small and reasonable key size when used alone. When combined to provide an ephemeral key wrapping function that continuously ratchets during the message phase, the entire message payload becomes a tremendously secure transmission with an inherent anti-cryptanalysis mechanism.
The Parano Protocol developed by the Paranotek, a company deals in products range from securing data storage, sharing and instant messaging to a variety of software utility tools that are based on post-quantum-computing resistant security protocols.
Users of Paranotek data-centric encryption tools enable organizations to overcome role-based security incompatibilities between IT vendors and multiple data providers to implement mandatory access control (MAC) versus discretionary access controls (DAC). The Parano ephemeral key wrapping technique can also enable multiple levels of security (MLS) within the data structure of a computer system to process information with incompatible classifications (i.e., at different security levels), permit access by users with different security clearances and needs-to-know, and prevent users from obtaining access to information for which they lack authorization.
Encryption History & Diversity
It is easy to guess who may want access to your private messages. We can speculate on what capabilities exist or who
may have the capacity to do decode today’s encryption keys, but we should just assume everybody can. But it isn’t hopeless.
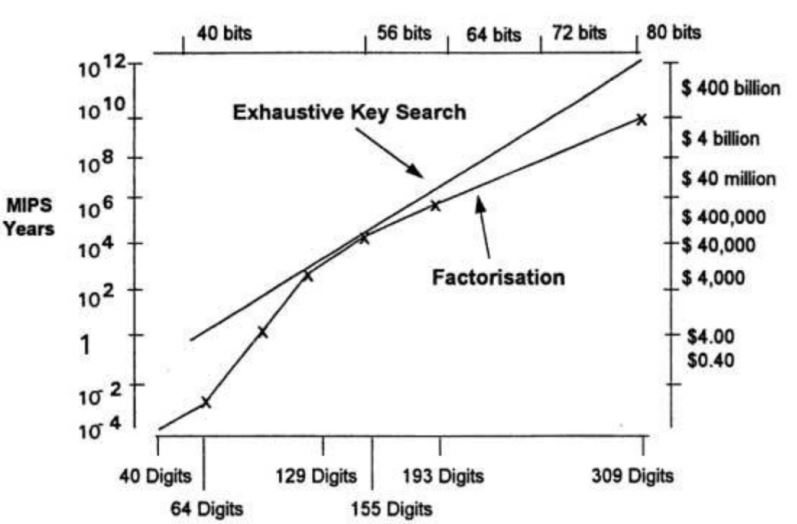
When security vendors talk about security protections one of the first buzzwords they use is the word encryption. That makes is safe right? They are using encryption. But are they still using linear congruential generators to generate pseudo-random numbers? Are they vulnerable to the birthday paradox? What about Post Quantum-computing resistant encryption?
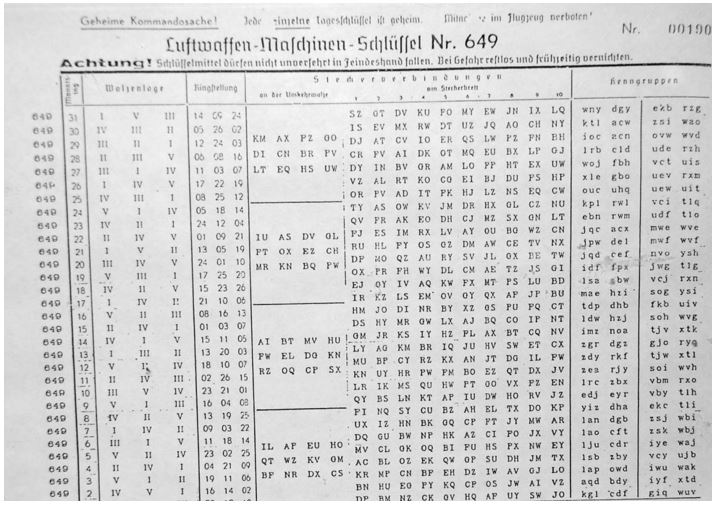
Most post-WWII encryption protocols have one thing in common. They use a 2-dimensional linear approach within their mathematical constructs. Early protocol theory was developed with computational efficiency in mind to be resilient to mathematically underpinnings and create useful key generation randomness capable of being mass produced. This key feature is called a pseudo-random number generation. Beyond the mathematical theory of encryption complexity comes the next largest challenge in an applied key generation, exchange, and storage.
Let’s use an analogy to parallel math and common sense. When you ask your local barista for a cup of coffee, common sense says you should be able to get a cup of coffee. Encryption like coffee is a very old business controlled by a brilliant few and they don’t like to be disrupted. The good news is if you know some basics, you will find yourself less vulnerable due to historical assumptions.
Did you assume your only option for coffee was iced instead of hot? How did you want that encryption? Did you want that encryption at the transport layer only or end to end? Did you want an in-band asymmetric handshake for your public/private key exchange? How about out of the band? SMS? Near Field Radio? Screen to screen?
When someone is using transport-layer encryption, they are putting trust in the company providing that service. For example, using HTTPS for their email means that they are trusting their email service provider to keep their user data safe from everyone, “except for people who work for the company” or the hackers who have spear phished an administrator or customer care representative. their “pwn’d” servers due to unpatched vulnerabilities is a classic cryptanalytic vector.
Using a multi-node VPN might mean that something and you are putting trust in the VPN service itself including all the company’s hosted servers. But if you are paranoid and demand privacy, end-to-end encryption is useful. You just need to know where the encrypted ends really are.
An end-to-end encryption protocol is a way of using encryption that ensures that information is turned into a secret message by its original sender (the first “end”) and decoded only by its final recipient (the second “end”). If your communication path has a server in the middle — you are open to interception by a wide variety of lawful and unlawful actors.
Let’s forgo the debate about intercepting the endpoints at this point. Most security protocols use a combination of the asymmetric and symmetric form of encryption processes. RSA+AES or RSA+ TWOFISH etc. Who may be in the middle capturing your encryption key exchange and what can they do to unwind your secrets inside your private conversation? What flavor of encryption is the most vulnerable and under what circumstances? Symmetric? Asymmetric? Elliptical Block Cypher? Steaming Cypher?
Let’s focus on the cryptology used in instant text messages as it is one of the most profiling user applications on the planet.
Asymmetric or Public Key Cryptography
Encryption has been around from a long time and the symmetric key or secret key cryptography has enjoyed a monopoly over most communications. Symmetric key meant using the same key to encrypt or decrypt a message.
The concept of Asymmetric Cryptography or Public Key Cryptography (“PKC”) emerged as a paper titled, “New directions in cryptography” by a Stanford University professor Martin Hellman and student Whitfield Diffie in 1976.
This is a two-key crypto-system where two parties engage in a secure communication over an open communications channel without having to physically share a secret key chart. The two different keys are used, one you share for encrypting the message, another you keep private for decrypting the message. The values of these keys are computationally and arithmetically intertwined.
Every recipient has to generate this set of two keys. The encryption key or the public key would be made available publicly. And the decryption key or the private key would be privately stored. Therefore, only the intended recipient can decrypt the message.
There are multiple asymmetric cryptography algorithms such as Digital Signature Algorithm (DSA), Elliptic curve cryptography, RSA or Diffie-Hellman. We will discuss RSA asymmetric algorithm. The RSA algorithm is the most widely used encryption algorithm in the world.
This document contains proprietary and confidential information related to the confidential environment, systems, and applications. It may also contain sensitive information from Paranotek. This document is not for re-distribution without written authorization.
To put the Parano Protocol into context, we need to review some history as most of the encryption approaches have much in common mathematically and are additive in the application.
RSA – 1982

RSA is a public-key encryption algorithm and the standard for encrypting data sent over the internet. It also happens to be one of the most common handshakes public / private key exchanges protocols. Unlike Triple DES, RSA is considered an asymmetric algorithm due to its use of a pair of keys. You’ve got your public key, which is what we use to encrypt our message, and a private key to decrypt it.
BLOWFISH – 1993
Blowfish is a single key algorithm designed to replace DES. This symmetric cipher splits messages into blocks of 64 bits and encrypts them individually. Blowfish is known for both its tremendous speed and overall effectiveness as many claims and that it has never been defeated. Meanwhile, vendors have taken full advantage of its free availability in the public domain. Blowfish can be found in software categories ranging from e-commerce platforms for securing payments to password management tools, where it used to protect passwords. It’s definitely one of the more flexible encryption methods available.
This document contains proprietary and confidential information related to the confidential environment, systems, and applications. It may also contain sensitive information from Paranotek. This document is not for re-distribution without written authorization.
TWO FISH – 1999
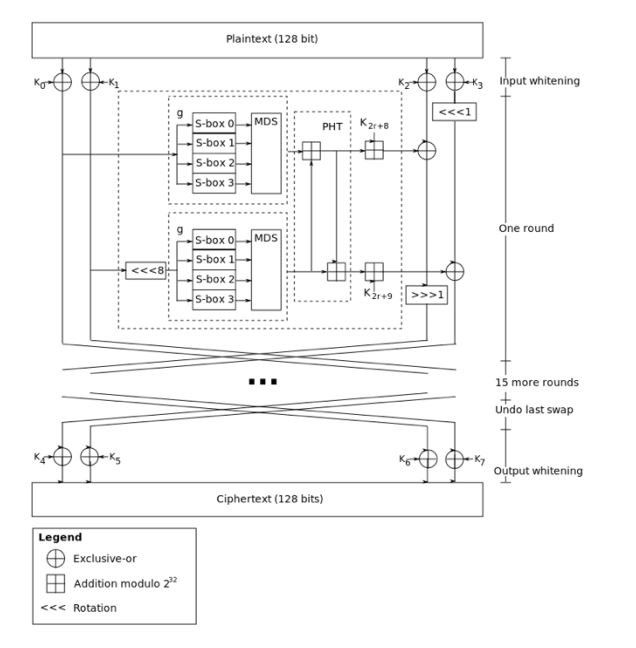
Computer security expert Bruce Schneier is the mastermind behind Blowfish and its successor Twofish. Keys used in this algorithm may be up to 256 bits in length and as symmetric technique, only one key is used. Twofish is regarded as one of the fastest of its kind, and ideal for use in both hardware and software environments. Like Blowfish, Twofish is freely available to anyone who wants to use it. As a result, you’ll find it bundled in open source encryption programs.
AES – 1997
The Advanced Encryption Standard (AES) is the algorithm trusted as the standard by the U.S. Government and numerous organizations. Although it is extremely efficient in 128-bit form, AES also uses keys of 192 and 256 bits for heavy duty encryption purposes. AES is largely considered impervious to all attacks, with the exception of brute force, which attempts to decipher messages using all possible combinations in the 128, 192, or 256-bit cipher.
Still, security experts believed that AES will eventually be hailed the de facto standard for encrypting data in the private sector. There are multiple variants of the AES protocol that leverage internal mathematical elements.
PPQE – 2018 (Post Quantum-Computing Encryption)
The Parano Protocol is a combination of four existing mature asymmetric algorithms used in a very deliberate way to bring existing computational resilience to affect while introducing variable complexity in key exchange to create a multi-dimensional computational problem to resist brute force attacks.
The well-known asymmetric encryption’s schemes in themselves are highly efficient and resilient relevant their reasonable key size when used alone, however, when combined to provide an ephemeral key wrapping function that ratchets during the message phase, the entire encryption package becomes a tremendously strong protocol with a built-in anti-cryptanalysis mechanism.
The diagram shown here is a simplified example of a single iteration with the encryption portion of the process. Each iteration in the message exchange uses key metadata from the previous package to derive the next package encryption function making the data stream encrypted and the stream key dynamic.
This is a more robust approach to securing a data exchange than using one or two locks and sets of keys. Simply put, when using a static linear congruential generator to derive the cryptographic register shifting or alphanumeric substitutions if you break the foundational master key or session exchange keys, you can decrypt any message that was used with that master key. With Parano, key usage is fluid and highly serialized and dependent on previous key iterations making the cryptographic register shifting dynamic.
Note: Above data provided by Paranotek
Other useful resources without spending a dime:
- How public key encryption works? A basic overview worth knowing
- What is VPN? How To use VPN? Why use VPN?
- How to encrypt personal files with 7-zip encryption
- WPA3 security protocol introduced by WiFi Alliance to enhance security
- BlackBerry new encryption technology can prevent hacking by a quantum computer




Related Posts
What is Identity Theft? All that you should know about this form of cybercrime
How to install BetterCap on Windows 11 or 10
Guardians of Data: How Role-Based Access Control Reinvents Security
Google to display only interest-based ads using a privacy sandbox
Ethical Considerations in Digital Banking: Privacy, Data Ethics, and Responsible AI
How to Check if an Android App is Safe to Download?