We have often come across the word encryption, some of us know about the meaning of this word, while many of us are unaware of it. In simple words, Encryption is the process by which digital messages are transformed into secret codes so that it remains safe and hidden until it reaches the receiver. So, this method converts a message sent by a sender so that it remains protected from all the cybercriminals and hackers out there until it reaches the receiver(s). The original message which is hidden in the encrypted text is called the ‘plaintext’, while its encrypted form is termed as ‘ciphertext’. Encryption can be made more and more complex by using advanced computer algorithms.
Encryption is used on the Internet to transfer data such as payment information, e-mails, or personal data confidentially and protected from manipulation. The data is encrypted using different cryptography methods based on mathematical operations. The research area that deals with these methods is called cryptography.
As of now, we have understood the basic meaning of Encryption, let us now try to find out how this process works? Well, Encryption is nothing but a game played by algorithms that hide your messages and transforms them into secret codes.
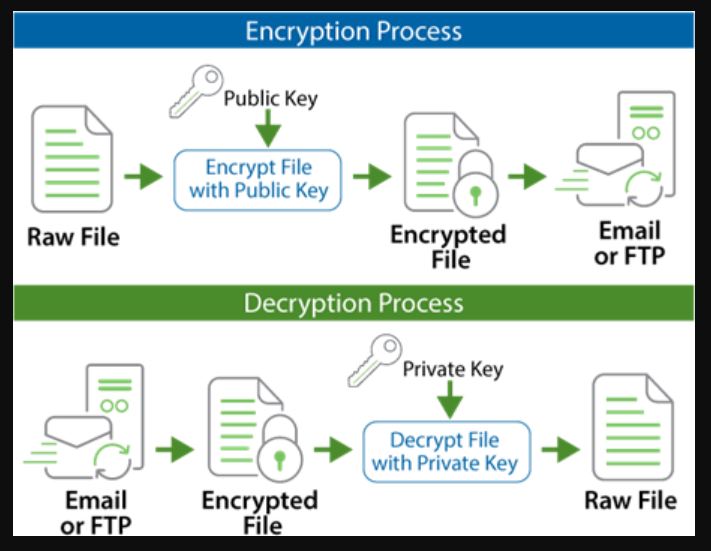
With the help of encryption, data can be transformed into a form that is no longer readable by unauthorized persons. Digital keys (key files) in symmetrical or asymmetrical encryption methods are used for encryption. Hybrid encryption methods combine both symmetric and asymmetric methods.
Symmetrical encryption method
Symmetrical encryption methods encrypt and decrypt the data with a single key. For this, the source and destination of the data must have the same key. If the secret key is passed on or if it is lost, the security of the data is no longer guaranteed. Critical actions for symmetric encryption methods are the distribution, storage, and exchange of keys.
Asymmetrical encryption method
Asymmetric encryption methods use two different keys. There is a public and a private key. The public key can be made available to everyone and is used to encrypt the data. The private key must be kept strictly secret. Only it enables the data encrypted with the public key to be decrypted.
The complex mathematical algorithms on which the asymmetrical processes are based mean that encryption and decryption require more computing capacity and are usually slower.
Hence, the receivers get their messages in the form of this code, and then they find out the meaning of this secret message by decoding it with the help of a secret key. Now, the complexity of these messages depends only on the type and level of algorithms involved there. Random number generators and computer algorithms are used to produce secret keys. But yes, all these keys are so programmed that they are indeed very hard to hack or predict. Keys are usually of two types:
Public Key
As the name suggests, this key is available publically for everyone to use. Anyone can access these encrypted messages by using these keys.
Private key
It is not available to the public and only the particular two or more parties involved have access to this key. It is also referred to as a Symmetric key.
We have now got some of the ideas about the definition and working of encryption, keys, and their types, etc. Let us now try to explore some more popular terms associated with Encryption.
Cipher
It is a type of algorithm used to hide to decode the message. It refers to the particular steps followed to encrypt or decrypt (bring the message to original form) the message. Block cipher and stream cipher are the two types of ciphers.
Algorithm
It is the process on which the entire encryption depends. It is a set of computer programs that are used to hide or encrypt the message or decrypt it. It is also termed as – code.
Decryption
This refers to the process of converting the encrypted text back to its normal form.
FAQs
[sc_fs_multi_faq headline-0=”h4″ question-0=”What is Encryption with examples?” answer-0=”Encryption is the process of hiding your digital messages in the form of secret codes until it reaches its destination. It is used extensively in communication, device such as smartphones, tablets, etc use encrypted data storage by default, files (encrypted by password), and much more. ” image-0=”” headline-1=”h4″ question-1=”How is Encryption done?” answer-1=”As discussed earlier, it is done with the help of computer algorithms, which hide your messages, then the receiver(s) can convert it back to its original form using secret keys. The more algorithms you employ, the more complex your message becomes.” image-1=”” headline-2=”h4″ question-2=” What are keys?” answer-2=”They are produced using random number generators and computer algorithms to help you convert the encrypted message back to its original form. They are of two types – Public key and Private key.” image-2=”” count=”3″ html=”true” css_class=””]
Related Posts
What is Encryption in Simple Words?
How to encrypt and password-protect PDF files in Microsoft Word
How to mount encrypted VeraCrypt or other volumes on an Android device
How to install VeraCrypt PIM encryption tool in Ubuntu Linux
How to use VeraCrypt encryption on PC to secure files
How to encrypt & decrypt files, videos, pictures in Android with a few taps